How to Use
Encrypt a file/folder
It is simple to use. All you have to do is drag and drop the file you want to encrypt onto the "AttachéCase" shortcut icon or the window that starts up.

Alternatively, if you already have a predetermined output file type, you can choose the output format first.

After dragging and dropping the file, enter the password. We recommend that you enter a long password that is difficult to guess.
Notice
In the old version (~ver.2), there was a limit to the number of characters that could be entered in the password, which was case-sensitive and limited to 32 single-byte characters (16 double-byte characters). But, in ver.3 and later, there is no such limitation.

Also in this screen, you can choose the output format by clicking on the AttachéCase icon.

Once you have entered your password and clicked the OK button, you will be prompted to enter the same password again for confirmation. This is to prevent you from encrypting with a wrong password and not being able to get it back.

Next, press the "Encrypt" button to start the process, and when you see the "Done" message, the encrypted file has been created.

Decrypt a file
As with encryption, this is done by dragging and dropping the encrypted file onto the attaché case icon, or onto an open window.

Attache case files, even if they have different extensions, are automatically identified as encrypted files by directly looking at the file data. So you can drag and drop a self-executing file to decrypt it without any problem.
If you can confirm that the file is encrypted, you will be asked for the password to decrypt it, as shown below.

When you see the word "Completed" the encrypted file should now be in the same original files location.

Self executable file
In the "Before Encryption" and "After Dragging and Dropping Files/Folders" screens shown below, select the following icons

![]()
The output will be an executable file (*.exe).
Notes on self-executable output
Public key cryptography
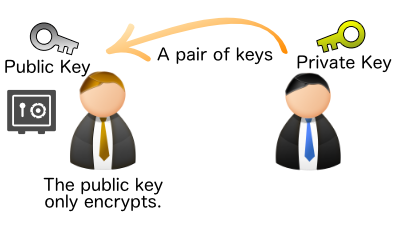
Public key cryptography is an encryption method that uses two key files to encrypt and decrypt.
Usually, the same password is used to encrypt and decrypt, as in symmetric key cryptography.

Public key cryptography refers to a set of "key bundles" in which the roles are divided into two parts: a password to perform encryption (file) and a decryption password (file).

In other words, even if you send a public key that can only be used for encryption, it is still safe, even if it is eavesdropped on, because it "can only be used for encryption. As long as the private key (for decryption) is at hand, the encrypted file cannot be undone.
First, generate a pair of public and private keys at hand.

Then, you send your "public key" to the person you want to exchange data with.
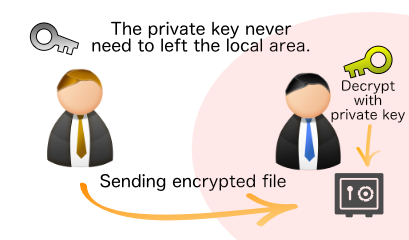
In this case, the private key is safe because it has not left its own local area.
Generate public and private keys
Now, let's actually encrypt and decrypt with public key cryptography in the AttachéCase. First, we need to generate a pair of public and private keys.

Select "Public Key" from the main window.

Click the "Generate Key" button, and then determine the file name and generate the public key and private key.

This will generate two files, one for the public key (.atcpub) and one for the private key (.atcpvt).
Encrypt files with a public key
Load the "public key (.atcpub)" file that you created earlier into the AttachéCase. At this point, the GUID, hash, and other information will be displayed, but if these values are communicated in advance to the person to whom you have given the public key by another means, the possibility of tampering will be reduced and the exchange will be more secure.

With this screen displayed, drag and drop the file you want to encrypt to complete the encryption.
Decrypt an encrypted file with a private key
A file encrypted with a public key can be decrypted by reading the "private key (.atcpvt)".

While in this screen, drag and drop the encrypted file to decrypt it.